
A series of targeted cyberattacks that started at the end of July 2024, targeting dozens of systems used in Russian government organizations and IT companies, are linked to Chinese hackers of the APT31 and APT 27 groups.
Kaspersky, who discovered the activity, dubbed the campaign “EastWind,” reporting that it employs an updated version of the CloudSorcerer backdoor spotted in a similar cyberespionage campaign from May 2024, also targeting Russian government entities.
It should be noted that the CloudSorcerer activity isn’t bound to Russia, as Proofpoint recorded an attack targeting a U.S.-based think tank in May 2024.
EastWind toolkit
The initial infection relies on phishing emails carrying RAR archive attachments named after the target, which employ DLL side loading to drop a backdoor on the system from Dropbox while opening a document for deception.
The backdoor can navigate the filesystem, execute commands, exfiltrate data, or introduce additional payloads on the compromised machine.
Kaspersky’s observations reveal that the attackers used the backdoor to introduce a trojan named ‘GrewApacha,’ which has been associated with APT31.
The most recent variant of GrewApacha features some improvements compared to the last analyzed version from 2023, including using two command servers instead of one, storing their address in a base64-encoded string on GitHub profiles from where the malware reads it.
Source: Kaspersky
Another malware loaded by the backdoor is a refreshed version of CloudSorcerer packed with VMProtect for evasion.
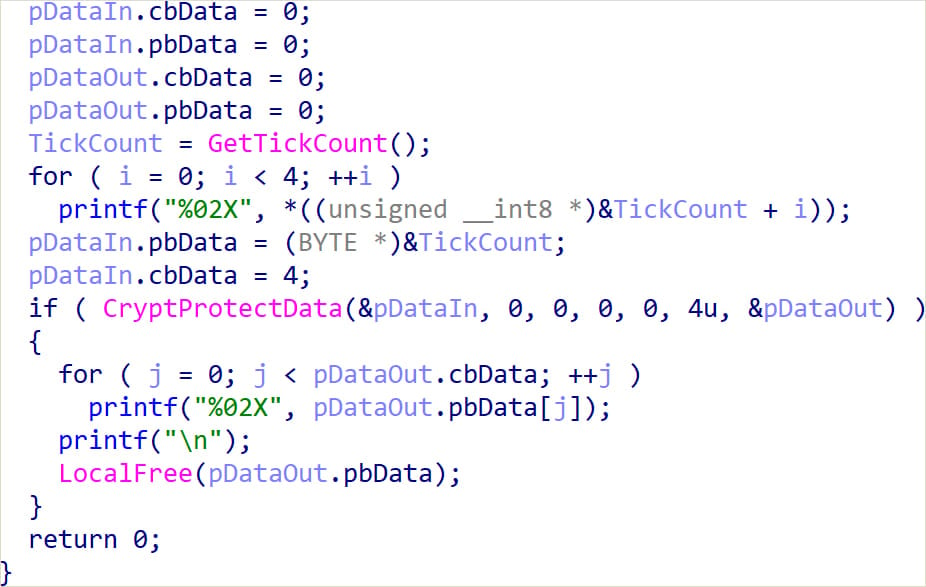
CloudSorcerer uses an encryption protection mechanism designed to prevent its execution on non-targeted systems by employing a unique key generation process tied to the victim’s machine.
Upon execution, a utility (GetKey.exe) generates a unique four-byte number from the system’s current state and encrypts it using the Windows CryptProtectData function to derive a unique, system-bound ciphertext.
If execution of the malware is attempted on any other machine, the generated key will differ, so the CloudSorcerer payload decryption will fail.
Source: Kaspersky
The new version of CloudSorcerer also uses public profile pages to get its initial C2 address but has now switched from GitHub to using Quora and the Russian social media network LiveJournal for this purpose.
The third implant seen in the EastWind attacks, introduced through CloudSorcered, is PlugY, a previously unknown backdoor.
PlugY features high versatility in its C2 communications and the ability to execute commands for file operations, shell command execution, screen capturing, key-logging, and clipboard monitoring.
Kaspersky’s analysis indicates that the code used in PlugY has been previously seen in attacks by the APT27 threat group.
Also, a library used for C2 communications through the UDP protocol is found only in DRBControl and PlugX, which are malware tools extensively used by Chinese threat actors.
Source: Kaspersky
Kaspersky comments that, as the backdoors used in the EastWind attacks are notably different, detecting them all on a compromised machine is challenging. Some things to look out for are:
- DLL files larger than 5MB in size in the ‘C:UsersPublic’ directory
- Unsigned ‘msedgeupdate.dll’ files in the file system
- A running process named ‘msiexec.exe’ for each logged-in user
The Russian cybersecurity firm concludes that APT27 and APT31 are likely working together in EastWind.
This case highlights the complex interplay between allied countries with strong diplomatic ties and common strategic goals yet active cyberespionage operations against each other.
Collaboration in economic, security, and military fields does not exclude intelligence agencies operating in the shadows from launching sophisticated and narrow-targeted espionage operations to collect valuable intelligence.
Note: This article have been indexed to our site. We do not claim legitimacy, ownership or copyright of any of the content above. To see the article at original source Click Here













