Khobeib Ben Boubaker
Head of Industrial Business Line Chez Stormshield
NETWORK EFFICIENCY AND SECURITY
Network segmentation is, first of all, very important for purely functional issues: availability and efficiency of equipment. When too many of them are connected on the same network and the flow of communication and private exchanges pour in, a “background noise” sets in. In an industrial world, for example, the PLC cannot ignore it: even if it does not process all the requests, it analyzes them systematically. This goes against the requirement of operational efficiency in this sector of activity. “This background noise diverts the automaton from its primary function, a situation which can very quickly lead it to saturation and therefore to malfunctions. A factory cannot therefore continuously grow its network architecture without segmenting it, ”testifies Vincent Riondet, Manager Delivery at Schneider Electric.
But it is on cybersecurity that segmentation brings its greatest benefit. Segmenting areas according to each person’s specific usage needs allows employees to only have the resources and access they need. Organizational, operational and automation-related data are thus contained in areas which may themselves contain sub-areas: thus segmented, they are less likely to leak or be compromised. “In order to achieve this division into homogeneous networks, it is necessary to carry out upstream a precise inventory of its equipment, of their types, to know the way in which they are physically connected to each other. All this information will make it possible to access a communication matrix and launch a risk analysis: this is essential to know how to prioritize and how to segment ”, explains Vincent Riondet.
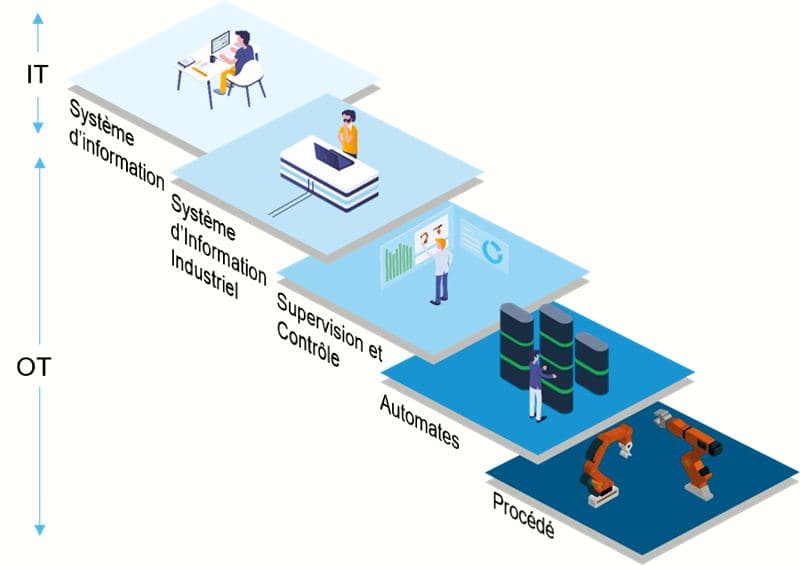
IT / OT: MULTIPLE LEVELS OF SEGMENTATION
In the beginning was IT. At the level of the information system of companies, first levels of segmentation are therefore necessary to separate certain groups of services or computers, according to their exposure to cyber threats – mainly linked to the connection to the Internet. In larger companies, we will thus tend to imagine internal segmentations to isolate services exposed to the Internet, staff computers, internal services, but also nomads and visitors.
At the same time, under the influence of the digital transformation of companies and the advent of Industry 4.0, industrial networks have evolved over time under the dogma of IT / OT convergence. “Initially, the industrial network was not connected with the IT system,” explains Tarik Zeroual, Country Manager at Stormshield. From now on, there is a real desire on the part of companies, for governance and business issues, to automatically collect information from the field: data related to operations, operation and maintenance are no longer sufficient. And for his part, the manufacturer now wants to know the frequency of use of his equipment, as well as all the information related to breakdowns and downtime of this same equipment ”. Establishing a barrier between the world of IT and OT therefore constitutes a fundamental level of security, in order to ensure cyber protection of industrial networks.
This convergence represents a a major challenge for most manufacturers, says Vincent Riondet. “The vast majority of our industrial networks are very poorly structured. They were installed and set up by automation engineers, so it is not their core business: they did not take into account the issues of IP addressing plan, broadcast, flow management, for example. . Their only objective was to make the equipment communicate with each other. ” A challenge all the greater as the threat does not necessarily come from very far. Plant employees and outsiders still often use USB keys, whether to collect data on the supervisory workstation or update PLCs. However, it is still common for these to be infected. A single connection could corrupt an entire information system. “This segmentation then makes it possible to guard against all internal and external threats, whether they come from the Internet or from external parties”, testifies Vincent Nicaise, Industrial Partnership and Ecosystem Manager at Stormshield.
SEGMENTATION: MORE THAN A RECOMMENDATION?
Network segmentation is therefore the measure most effective for containing cyber threats and preventing malware from spreading within an IT or operational infrastructure.
It is also one of the flagship recommendations of the IEC 62443 standard. This industrial cybersecurity standard developed the concept of the distribution of “zones” and “conduits” according to the criticality levels of dedicated equipment. A defense-in-depth logic which, thanks to the integration of firewalls, strictly and unchangingly determines the authorized and unauthorized communication flows between predetermined segments or blocks. Divided into blocks, the network becomes more difficult to attack as a whole by a cyber criminal.
Simply recommended by the texts of the IEC 62443 standard, segmentation turns out to be an essential bulwark to limit intrusions and deal with cyber attacks. Like wearing a seat belt in the car, this technique is imperative to implement – regardless of the type of network concerned.
A PHYSICAL OR VIRTUAL SEPARATION
There are two methods of segmentation: a segmentation physical and virtual segmentation. Physical segmentation consists of creating parallel networks so that they are completely separate. A switch will be installed for each category of machine – PLC, PC, printer, etc. Virtual segmentation, on the other hand, offers the same hardware switch for the different devices: connected to different ports of the switch, these are virtually separated by virtual networks (VLAN) simulating separate switches, thus making it possible to segment a physical network of logical way. They cannot communicate with each other, unless they are linked with a firewall that allows them.
“Both methods have proven their worth in segmentation, one is not more vulnerable than the other in cyber matters, if they are well done. The only difference, in my opinion, is in terms of cost. Physical segmentation requires the purchase of many new materials. Very few companies can afford this luxury. Virtual segmentation is the most economically viable ”, specifies Tarik Zeroual.
NAT, A MECHANISM THAT CAN COME UP USEFUL
The implementation of network segmentation, whether virtual or physical, requires, in some cases, a change in the organization of the addresses used by the devices to communicate with each other. In fact, factories initially deployed equipment according to operational need without taking into account the allocation of IP addresses. The network being “flat”, all the devices could communicate without any problem. “But with the segmentation into zones, the devices can only communicate with those who are in the same zone, the same subnet. However, it is impossible to ask a factory that has spent fifteen years developing its industrial systems to reconfigure this equipment one by one, and test again that everything is working. It would be a financial pit for her, “explains Vincent Riondet.
Also, to remedy the problem in the short term, it is possible to use the NAT (Network Address) function. Translation): this system makes it possible to “transform” addresses, to match IP addresses to other IP addresses. “This function consists of translating an address from one subnet to an address in another subnet to ensure interconnection. It allows you not to touch the applications and not to have to configure them again. NAT can be likened to a temporary solution which therefore allows information to pass through while waiting for the modernization or replacement of industrial systems, continues Vincent Riondet. We have clients for whom this migration scenario spans two years. However, we have already laid the foundations for these future reconfigurations, defined our targets and our segmentation strategy. But behind, it takes time on each maintenance stop. The industrial sector is complex, we have to move forward little by little. Without NAT, the majority of industries would not be able to secure their systems. ” Address translation (or translation) also makes it possible to integrate an industrial subsystem into the overall operational infrastructure without losing the certification of the manufacturer or the service provider.
On l ‘has therefore seen: the segmentation of the information system is a complex operation, which requires time. With a view to defense in depth, it is therefore imperative to get started without further delay!
Note: This article have been indexed to our site. We do not claim ownership or copyright of any of the content above. To see the article at original source Click Here















