My biggest take-away from over two decades in cybersecurity? The most elegant solution are ones that are simple to implement, have an element of automation and are easily incorporated into existing activities seamlessly. With digital innovation leading to accelerated and automated DevOps, one of the most important things we can do to reduce risk in the enterprise is to begin to incorporate cybersecurity into enterprise CI/CD pipelines. Now, as breach attack simulation and automated purple teaming becomes strategic to reducing risk and optimizing security controls in a continuous security validation fashion, these offensive testing techniques can be incorporated as well. For cybersecurity managers and business leaders, adoption of these solutions means they know what portions of their cybersecurity investment to keep and what to get rid of. Their spend is optimized. They can effectively measure, explain, and reduce cybersecurity risk. For cybersecurity practicians, when done right, these solutions allow you to optimize your security controls, your incident response processes, and train your personnel.
In adopting both technologies there are four key caveats in best practice adoption:
- Ability to utilize existing cyber workforce: With a large global shortage of highly skilled cybersecurity professionals the solution must be useable and accessible to a wide array of skill sets.
- Adopted in a continuous security validation manner: The platform must be updated daily, automatically, and capable of being run in a continuous security validation fashion.
- Actionable intelligence updated constantly: Since threat actors change and evolve daily, there are inherent needs for these solutions to make new intelligence immediately actionable by adding new tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to the solution when discovered.
- Comprehensiveness: These solutions must be able to test in production safely using real workloads and real tests across all stages of the kill-chain. It needs to include reconnaissance checks of enterprise against darknet and Internet INT and OSINT. It must include phishing campaigns against the enterprise staff. Attacks must include pre-exploit and post exploit and be able to work across your entire environment from legacy premises, virtualized, cloud, SaaS, and containers.
Incorporating into the CI/CD Pipeline
The main tool of someone in DevOps is to utilize play books. Whether Chef Puppet or Ansible, these play books provide seamless integration automation allowing entire environments and thousands of servers to be implemented in a matter of a few mouse clicks. Cymulate’s well documented API set means the DevOps professional can easily create in a CI/CD pipeline image, spin it up, and test it against thousands of the most recent attack tactics, techniques, and procedures (TTPs) and indicators of compromise (IoCs). Based on the resulting rating, the DevOps professional can easily make a go/no go decision on whether that image becomes implemented into production or whether it returns to the development environment for increased tuning. The Cymulate solution, which ties into hundreds of security control solutions, not only provides prescriptive, easy to follow remediation advice on how to shore up security controls but executive summary reports as well.
For the article, Cybersecurity Researcher Michael Loffe and I ran an image build using Jenkins, the well-known, free, and open-source automation package. In Example Image 1 below, as part of the Jenkins build, we added an assessment to check against Cymulate’s Purple Team module being pulled up via REST API key looking for a 40% or better success rate percentage to give the build a passing grade.
Example Image 1
In the initial run we see the test image spun up and was tested against Cymulate’s Purple Team module. Looking at the Console Output, the score is greater than the 40% success rate threshold and the build received a failing grade and was returned for better tuning to be tested again. (See Example Image 2).
Example Image 2
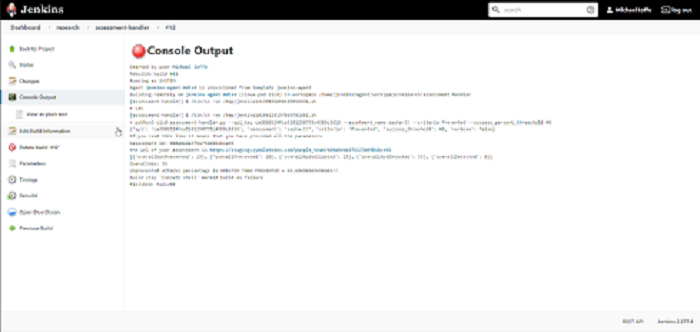
This example is elegant, simple, and only adding 3.5 seconds to the build time — adoptable. By incorporation into any DevOps CI/CD pipeline we can add purple teaming tests that will result in tighter image and third-party security controls while keeping the speed and simplicity intact. Subsequent runs of the tests after controls were tightened show risk was ameliorated to an acceptable level and that the workload is pushed it to production. By accomplishing this we have incorporated purple teaming into the shift left, CI/CD pipeline. Digital innovation with all its speed and agility CAN be accomplished hand in hand with cybersecurity.
One of the newer players in the field Cymulate is already one of the largest. In a third-party comparison of vendors, Cymulate won Frost & Sullivan’s Best Practices in Global Breach and Attack Simulation scoring first in innovation and second in business expansion and market share.
For more Information, visit www.cymulate.com and register for a Free Trial.

Dave Klein is the Director of Cyber Evangelism for Cymulate. With more than 21 years of real-world cybersecurity experience, he works with Cymulate teams, customers and industry thought leaders to address the challenges of securing modern enterprise environments. Dave’s long career includes working on the NIST response to President Obama’s Policy Directive 21 on Critical Infrastructure Security and Resilience, leading some of the largest sales engagements for US Federal security solutions, and working with the City of New York post 9/11, helping shore up defenses.
Note: This article have been indexed to our site. We do not claim ownership or copyright of any of the content above. To see the article at original source Click Here

.jpg)










